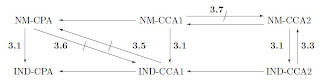
The goals = { IND, NM }
The attacks = { CPA, CCA1, CCA2}
The notions = goals * attacks = {IND-CPA, IND-CCA1, IND-CCA2, NM-CPA, NM-CCA1, NM-CCA2 }
Let A and B be any two any two notions from the above set.
A => B holds if X is any encryption scheme meeting the notion of security A then X also meets the notion of security B. (In other words, B providers stronger notion of security compared to A)
In the above diagram there is an arrow (normal or hatched) if and if implication between two security notions holds.
Refer to [1] for more information.
[1] Relations Among Notions of Security for Public-Key Encryption Schemes, 1999, M. Bellare et.al.
No comments:
Post a Comment